The Cloud Shift Created New Attack Surfaces And New Opportunities for Attackers
Modern infrastructures are no longer isolated networks, they are cloud-native, API-driven, and globally interconnected. While the cloud accelerates innovation, it also concentrates risk, expands external attack surfaces, and creates complex permission models that attackers know how to exploit.At NotLAN, we approach cloud security offensively:
We simulate how real attackers think, move, and escalate inside your cloud environments.


Cloud Penetration Testing
• External perimeter assessments targeting exposed cloud assets
• Cloud-based web application and API penetration tests
• Enumeration of misconfigured services, exposed storage buckets, and orphaned resources
• DNS, CDN, WAF, and firewall bypass techniques

• Assessment of IAM roles, policies, permissions, and privilege escalation paths
• Abuse of over-permissive roles, service accounts, and cross-account trust relationships
• Token theft, credential abuse, key exposure, and session hijacking scenarios
• Cloud provider-specific privilege escalation pathways (AWS, Azure, GCP)

• Secure architecture assessments aligned with best practices
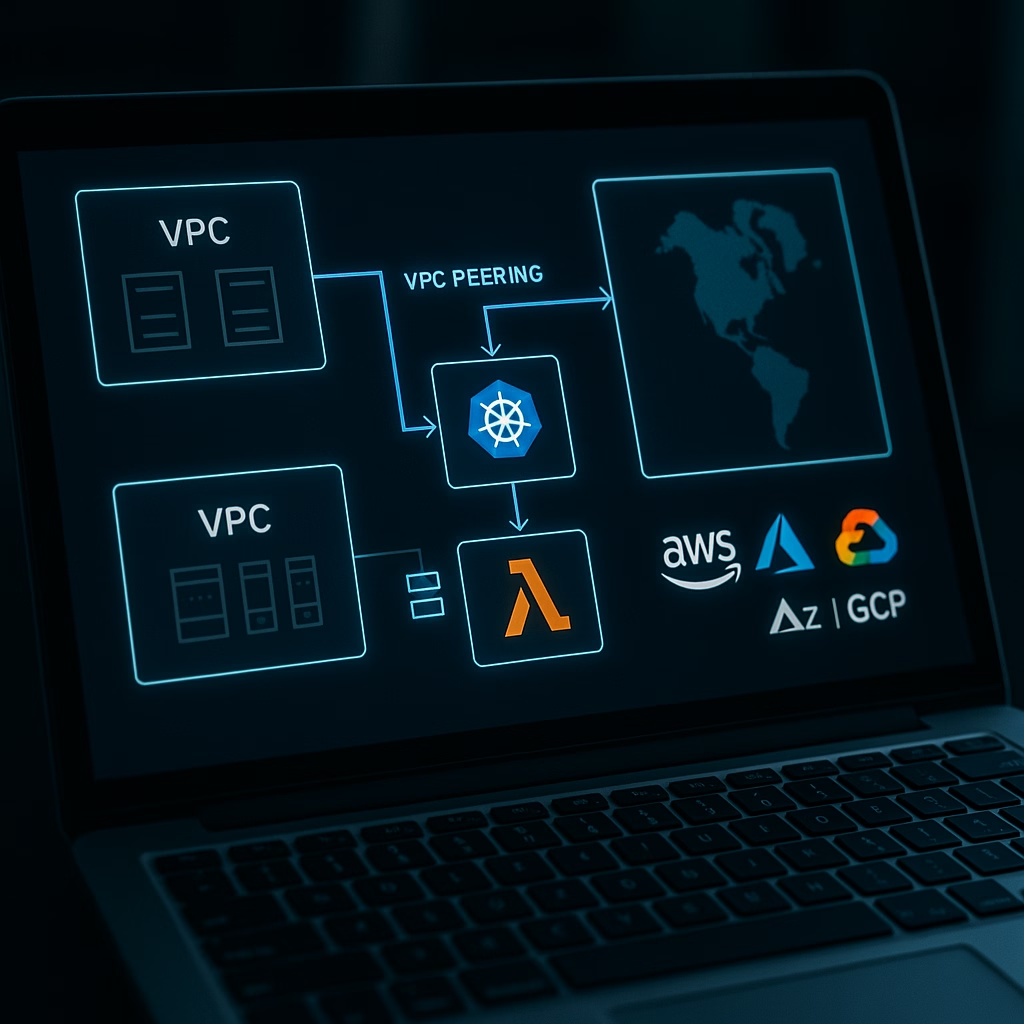
• Review of network segmentation, VPC peering, private endpoints, and VPN configurations
• Serverless, container orchestration (Kubernetes, ECS, AKS, GKE), and workload isolation evaluations
• Assessment of backup, disaster recovery, and high availability configurations for security weaknesses
• Lateral movement simulations within cloud control planes
• Exfiltration of data via cloud-native services
• Detection of persistence mechanisms inside cloud workloads
• Simulation of advanced threat actors leveraging compromised cloud credentials
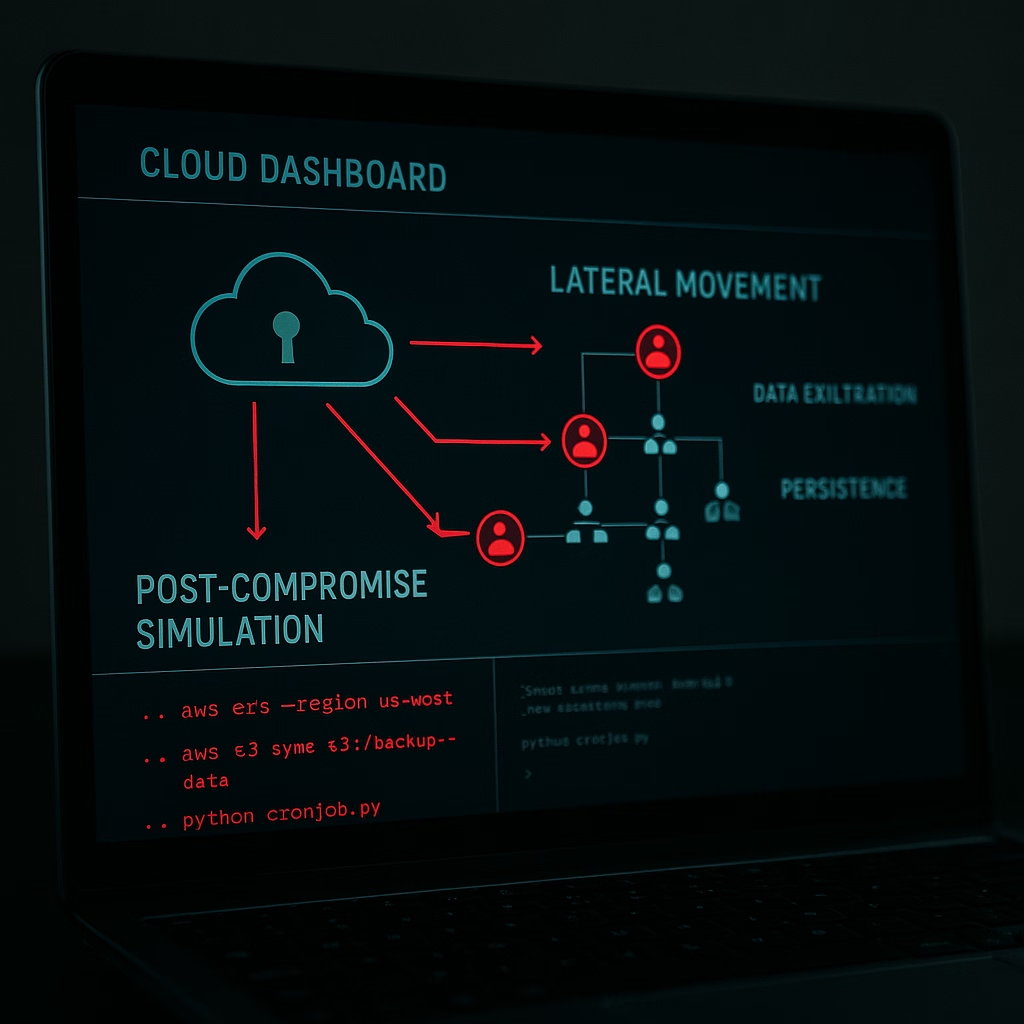
• MITRE ATT&CK for Cloud: adversary TTP mapping across AWS, Azure, and GCP
• OWASP Cloud-Native Application Security Top 10 (Cloud-Native AppSec Top 10)
• OWASP Top 10: applicable to cloud web applications and APIs
• CIS Benchmarks for AWS, Azure, and GCP
• PTES methodology extended for cloud infrastructures
• Custom threat modeling based on your cloud stack and risk profile

• Amazon Web Services (AWS)
• Microsoft Azure
• Google Cloud Platform (GCP)
• Hybrid & Multi-Cloud Environments
• Cloud-Native Kubernetes Orchestrations (EKS, AKS, GKE, OpenShift)

✅ Offensive security approach focused on real attacker behavior, not checklist audits
✅ Full lifecycle testing: external perimeter, identity abuse, internal escalation, and data exfiltration
✅ Cloud-native privilege escalation simulations based on real-world adversary tradecraft
✅ Deep understanding of how cloud control planes can be abused at scale
✅ Direct collaboration with cloud architects and DevOps teams for actionable remediation
